Security Signals Tax Clients Actually Notice (and Trust)
When clients hesitate to upload a W-2 or sign Form 8879, it’s rarely the math—it’s trust. The fastest path is to make security visible in plain English at the exact moment they must act (open link, send a file, sign). Below are vendor-agnostic signals you can ship this week—no portals required.
7 trust signals clients scan in 3 seconds
Recognizable sender
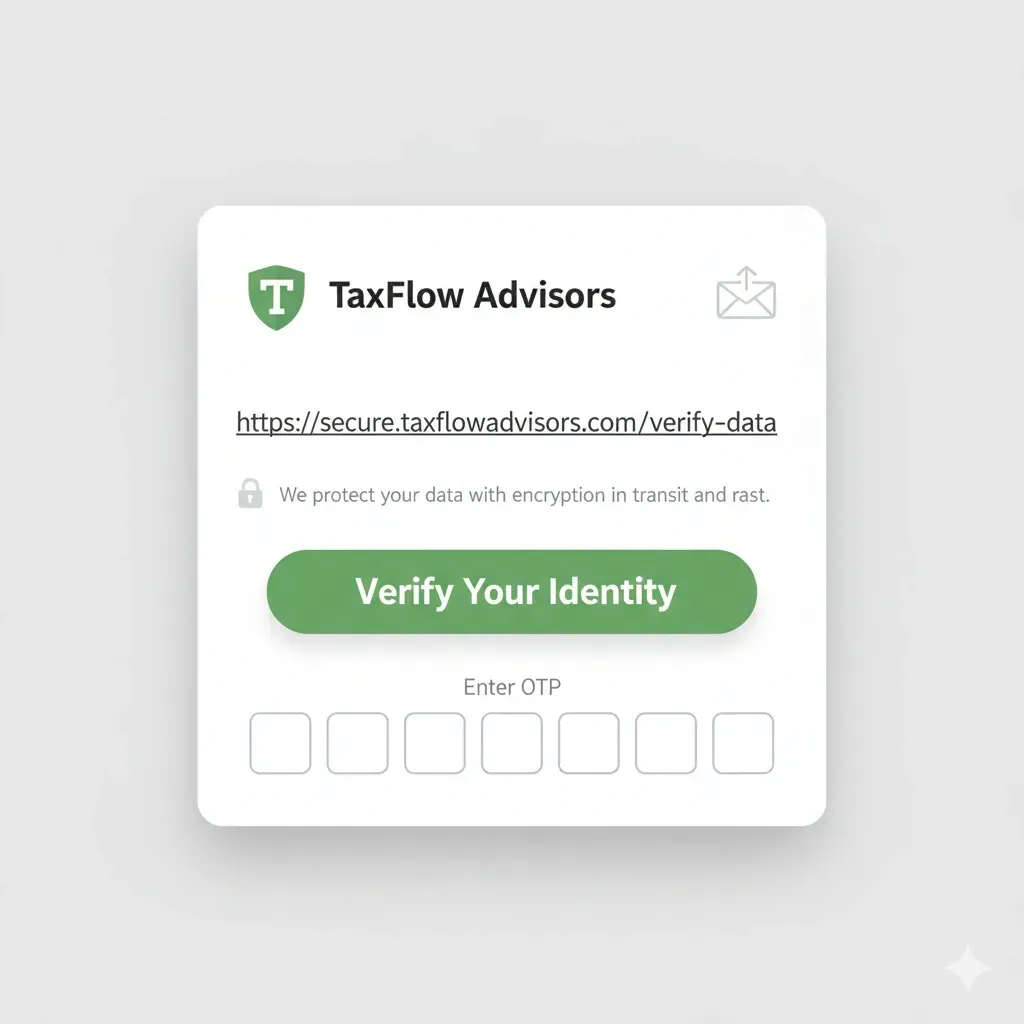
From-name and email that match your firm (no generic noreply). Consistent signature and contact line that invites replies.Plain-English “why this is safe” line near the button
One sentence clients understand: “We protect your data with encryption in transit and at rest.”Link clarity
Avoid shady shorteners. Show the destination domain in full. Add a brief line like “This link expires in 24 hours.”Review screen before e-sign
Summarize what’s being signed (form name, year, amount if relevant) and the next step.One-time code for sensitive actions
SMS or email OTP for approvals or signatures. Clients equate a code with serious security.Timestamped confirmation
After upload or e-sign, send a receipt with “what, when, who” (e.g., “Signed by Ana G., 2:14 PM ET, Sep 17”).Fast path to a human
A visible “Reply to this email” or phone line on every request lowers suspicion and reduces back-and-forth.
Before → After (how it feels to a client)
Before: generic sender, shortened link, technical jargon, vague “Sign here”.
After: recognizable firm, clear destination link, 1-line security reassurance, review screen, OTP, timestamped receipt.
Ship it in one week (quick wins)
Standardize request templates (email/SMS) with a one-line security explainer and clear action verbs: “Upload 1099”, “Sign Form 8879”.
Enable OTP (code via SMS/email) for signatures or key approvals.
Turn on receipts that include timestamp and document name.
Add link expiry (24–72h) for one-time upload or sign links.
Name owners: “Questions? Reply to this email. María (Client Ops) will respond within 1 business day.”
Example microcopy you can copy-paste
At the request button: “Your data is encrypted in transit and at rest.”
At e-sign review: “You’re signing Form 8879 for Tax Year 2024. You’ll get a timestamped receipt.”
After upload: “Received: W-2 from Alex R. at 3:07 PM ET. We’ll review within 1 business day.”
On link lines: “This link is unique to you and expires in 48 hours.”
Checklist (print this)
FAQ
Will extra security slow clients down?
Not if it’s obvious and short. One code + one sentence of reassurance beats a confusing flow with no explanations.
Do clients read long policies?
No. They skim signals: sender identity, clear link, brief security line, review screen, OTP, and a receipt.
Do I need a portal for this?
No. These signals work in email templates, secure links, and e-sign flows—whatever tools you’re using today.